INCS: In-network Caching Shelter for e-commerce bot traffic
INCS: In-network Caching Shelter for e-commerce bot traffic
Work by Masoud Hemmatpour, Changgang Zheng and Noa Zilberman
E-commerce bot traffic
Among industries, e-commerce sees a wide range of bot attacks. E-commerce ranks fifth in the intensity of bad bot traffic and first in the volume of sophisticated bot traffic. Companies like Amazon face a persistent challenge with bot traffic, given that 70% of their total traffic is generated by bots, resulting in significant economic consequences. There are different types of bots which can cause problems for e-commerce such as manipulating product ranks and increasing data access latency. Despite e-commerce businesses’ continuous efforts to enhance user experience through the adoption of modern technologies, the disruptive presence of malicious bots poses a significant threat to the revenue and overall success of companies.
In-network cache poisoning
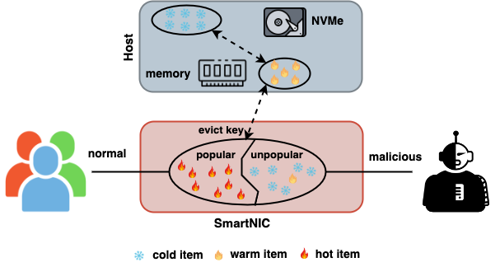
We review the characteristics of bot traffic in real-world e-commerce websites and analyze how these characteristics can bring vulnerability while using in-network caching in the backend. We outline how the presence of bot traffic can lead to higher cache misses of legitimate users. As depicted, regular users typically request popular items, leading to the storage of these items within the in-network caching system. However, malicious bots follow a different pattern, actively soliciting less popular items and attempting to inject counterfeit popular items into the caching system. The introduction of this injection results in the removal of popular accessed items, leading to a notable rise in data access latency for normal clients.
In-network Caching Shelter (INCS)
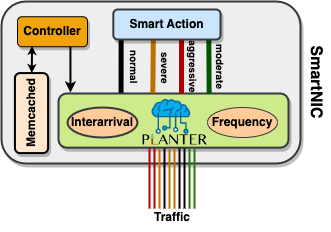
In this work, we propose In-network Caching Shelter (INCS), a mitigation solution for attacks on in-network caching. To safeguard the caching system, an in-network machine learning framework (i.e., Planter) is used to classify incoming requests, detecting and acting on bot-generated queries. INCS runs on a programmable network target, such as a Data Processing Unit (DPU) or SmartNIC using Behavioral Model Version 2 (BMV2) or Open vSwitch (OvS).